- John The Ripper Crack Sha512 Encryption Pdf
- Sha512 Decrypt
- John The Ripper Crack Sha512 Encryption Key
Office Encryption: The slow hash-cracking is the result of efforts the Microsoft Office application puts into storing the password hash and encrypting the document. The encryption methods are far more complex than they used to be in earlier Office versions. Office 2013 encryption uses 128-bit AES using SHA-512 algorithm. In this mode John the ripper uses a wordlist that can also be called a Dictionary and it compares the hashes of the words present in the Dictionary with the password hash. Example In this case we have a custom wordlist, and a hash that we need to compare.
In this post I will show you how to crack Windows passwords using John The Ripper.
John the Ripper is a fast password cracker, primarily for cracking Unix (shadow) passwords.Other than Unix-type encrypted passwords it also supports cracking Windows LM hashes and many more with open source contributed patches.
Now lets talk about the password protection method used by Windows. Windows user account passwords are typically stored in SAM hive of the registry (which corresponds to %SystemRoot%system32configSAM file), in the SAM file the password is kept encrypted using the NTLM hash is very well known for its cryptanalysis weaknesses.
The SAM file is further encrypted with the SysKey (Windows 2000 and above) which is stored in %SystemRoot%system32configsystem file.During the boot-time of Windows the hashes from the SAM file gets decrypted using the SysKey and the hashes are loaded to the registry is then used for authentication purpose. Both system and SAM files are unavailable (i.e, locked by kernel) to standard programs (like regedit) during Windows’ runtime .
As told earlier NTLM hash is very weak for encrypting passwords.The NTLM encryption algorithm is explained below :
- ASCII password is converted to uppercase
- Padding with null is done until 14 bytes
- Split it in two 7-byte arrays
- Pad both to make 64 bits (8-byte) which will be used to create a DES key
- DES-encrypt the string “[email protected]#$%” using the array as key for each 7-byte array (results 8-byte stream)
- Join 2 cipertexts which forms the NTLM hash (16-byte)
Major pitfals of NTLM hash
- ASCII is not Unicode
- Uppercase reduce complexity
- LM fails with passwords length more than 14 characters
- Salting is not available
- It is easy to determine whether the password is less than or more than 7 characters
Cracking Windows Passwords John The Ripper
For the sake of demonstrating this I had already set a dummy account called demo and allotted a password iRock to it, which will be cracked later-on.
User Accounts showing demo user
I booted using the Ubuntu LiveCD and mounted my Windows partition - /dev/sda1
Then copied SAM and system files to /home/prakhar
Then installed samdump2 and John The Ripper :

Then dumped the syskey and NTLM hashes from system and SAM file, respectively :
NTLM hashes recovered from SAM file
I then bruteforced the password using John The Ripper :
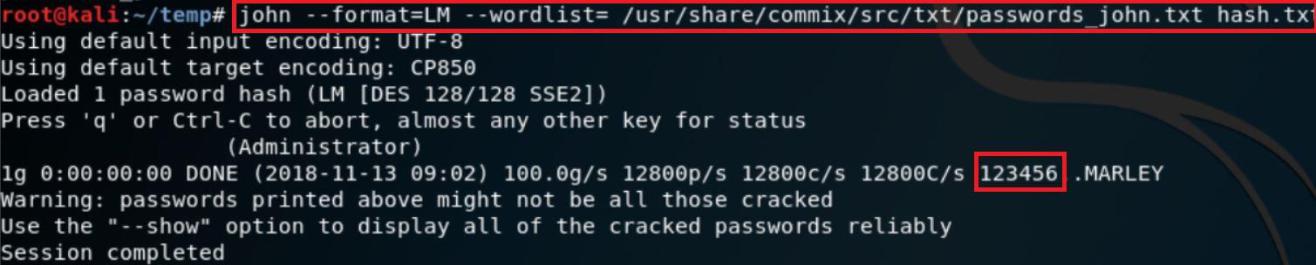
You can clearly see above, JTR has cracked the password within matter of seconds, I aborted the session in between since password was already recovered. Mission accomplished !
I just spent at least 15 minutes trying to figure out why every single post on the Internet tells me to place MD5 hash in a file and call John like thisJohn The Ripper Crack Sha512 Encryption Pdf
john --format=raw-md5 --wordlist=/usr/share/dict/words md5.txtand yet, it constantly gives me an error message:
No password hashes loaded (see FAQ)The content of md5.txt was:
20E11C279CE49BCC51EDC8041B8FAAAAI even tried prepending dummy user before this hash, like this:
dummyuser: 20E11C279CE49BCC51EDC8041B8FAAAAbut without any luck.
And of course I have extended version of John the Ripper that support raw-md5 format.
It turned out that John doesn't support capital letters in hash value!
Sha512 Decrypt
They have to be written in small letters like this:20e11c279ce49bcc51edc8041b8fbbb6
John The Ripper Crack Sha512 Encryption Key
 after that change, everything worked like a charm. What a stupid error!?
after that change, everything worked like a charm. What a stupid error!?